In Automating my Home Network – Part 1, I explained that I am going to build up an automation workflow which will create a digital twin of my production home network.
My plan was to use Containerlabs to achieve this feat, but alas, it was not meant to be.
I am not sure why I could not get a FortiGate and Aruba CX image to deploy in Containerlabs using the vrnetlab project, but after trying and failing, I decided to go a little more old fashioned.
Virtual Machines!
Therefore in this blog post, I am using Ansible to provision VMs in my lab, which uses a opensource hypervisor called Proxmox. Now before I jumped straight into trying to work out how to deploy a FortigateVM into Proxmox, I figured I should try and get a simple VM deployed.
So just so you are not disappointed after reading this, My next post will be about deploying a FortiGateVM on Proxmox, and hopefully, that will also include a base configuration.
But let’s start small…
What is Proxmox?
Proxmox is a virtualisation platform which is very popular in home lab setups and small to medium-sized businesses.
You may have heard of VMWare ESXI. Since this platform is no longer available for free, Proxmox has grown in popularity for it’s free version.
I have come across very few limitations to using Proxmox for my lab. However one common problem I come across is that whilst a lot of networking vendors provide VM versions of their products, some only support ESXI. Whilst I am sure there is a way to convert these. I have not had the time to really work that out.
What is Ansible?
If you have never heard of Ansible, it is an open-source automation tool owned by IBM. It is commonly used to manage infrastructure. Ansible uses YAML to define the tasks required in playbooks. Playbooks define the desired state of systems and can be used to configure deploy and orchestrate complex workflows across multiple systems.
It is assumed for this post that you already have some knowledge of ansible and already have it installed on your system.
Setting up Proxmox for Ansible
The magic of Ansible is that it can just use SSH, so you can likely manage a lot of systems without additional packages for accessing the system. But for us to be able to use the modules built to manage Proxmox, we need to install a wrapper for the API, called proxmoxer.
Now we could just manually login to our Proxmox nodes and install proxmoxer. However given we are trying to automate things here, let’s do it through ansible.
I have to attribute most of the steps below to https://www.techtutorials.tv/sections/promox/proxmox-how-to-automate-using-ansible/
Prerequisites
- ansible
- sshpass
Setup the ansible user
Using the root account to manage anything is never a good idea, therefore my first step is to create a new user on my cluster, this user will authenticate via an SSH Key which I have already generated.
👉 sshpass is used to allow for an interactive password prompt so we don’t need to put our root password in the ansible files.
So let’s first build our inventory file at the root of the Ansible directory structure.
[nodes]
192.168.1.10
192.168.1.11Now let’s create a playbook to login to the cluster, create a new ansible user, add the key to the authorized key file.
Create a file called onboard.yml
---
- hosts: nodes
tasks:
- name: create ansible user
user:
name: "{{ ansible_pve_user }}"
shell: '/bin/bash'
- name: add ansible ssh key
authorized_key:
user: "{{ansible_pve_user}}"
key: "{{ ansible_ssh_key }}"You will notice that I am using variables in the playbook, I have defined these in group_vars/all.yml
ansible_ssh_key: " Your SSH Key here"
ansible_pve_user: " Your Username here"We also need to give our new user some superuser permissions and specify NOPASSWD when running elevating using sudo.
To do this, we will create a new text file which includes the desired configuration and then this file will be copied onto the proxmox hosts we defined in our inventory file. The playbook will copy this file into a sudoer file named after our ansible user.
Create a new directory called files, and make a new text file called to hold the configuration, mine is called sudoers_ansible_permissions
Copy the configuration below and paste it into the configuration file:
"Your Username here" ALL=(ALL) NOPASSWD: ALLRename “pve-ansible” to a username of your choosing.
Save the file.
Add the following at the bottom of your onboard.yml file:
- name: add ansible to sudoers group
copy:
src: files/sudoers_ansible_permissions
dest: /etc/sudoers.d/"{{ ansible_pve_user }}"
owner: root
group: root
mode: 0440Save the playbook and we can try running against the promox cluster.
ansible-playbook onboard.yml -i inventory --user=root -kYou will see ansible go off and run through the tasks. After which it will tell you if the changes were successful or not.
To test access, run the below to test using the ansible ping module. Be sure to use your username and private key.
ansible nodes -m ping -i inventory --user="Your Username" --private-key ~/.ssh/"Your Private Key"Setup and Install Proxmoxer
The Proxmoxer module uses the Proxmox REST API to manage the infrastructure. Therefore although we can now login using SSH in order to install the proxmoxer package on the nodes, we still need to create an API token for our Ansible Playbook to use when calling the promoxer package.
Creating an API token in the Proxmox GUI
- Firstly, Login to the Proxmox GUI for your cluster.
- Under Datacenter, you will see Permissions and then Users
- Create a new user which matches the username defined earlier.
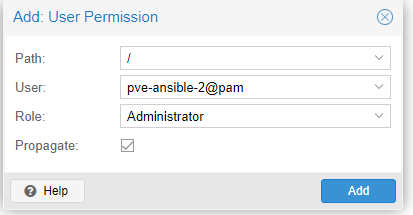
- Now move to Permissions and grant the user the access. Now I have allowed admin access because this is a Lab, In production you would limit this as much as possible.
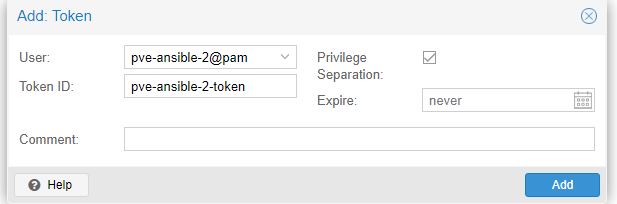
- Create a new API token, Under API Tokens – You will be presented with the token value, make sure you save this!
Installing Proxmoxer
Here I am using another playbook for the specific usecase of installing proxmoxer. It is using the apt repository to install the python3-proxmoxer package.
👉 This is not the only way to install proxmoxer, check out the documentation on installing -https://proxmoxer.github.io/docs/2.0/
Here is the playbook – I called this one install_promoxer.yml
---
- hosts: nodes
become: true
tasks:
- name: update repository cache
apt:
update_cache: yes
cache_valid_time: 3600
- name: Install Proxmoxer
apt:
name:
- python3-proxmoxer
state: latest
And that’s it, Now run the playbook using the ansible user and private key you installed earlier and we can move on to actually spinning up a VM using Ansible!
ansible-playbook install_proxmoxer.yml -i inventory --user="Your Username" --private-key ~/.ssh/"Your Private Key"
Testing
You can create a quick playbook to test the creation of a VM, to make sure nothing errors out.
---
- hosts: "HOST IP or Group"
become: false
gather_facts: false
tasks:
- name: create new vm with minimal options
vars:
ansible_python_interpreter: /usr/bin/python3
proxmox_kvm:
api_user: "username"
api_token_id: "token id"
api_token_secret: "token value"
api_host: "Host IP"
node: "node you want to deploy to"
name: vmtest #Name of the VM
ansible-playbook pve_create_vm.yml -i inventory --user=ansible --private-key ~/.ssh/ansible-key
And that’s it. I really hope this has helped you.
I have not got around to setting up blog subscribers, but if you would like to follow along, I will be posting blog updates on LinkedIn, pop over and hit the follow button!
In the next post I am going to use Ansible to automate the provisioning of the FortiGate Firewall VM that will be used in my lab network.

