Introducing SASE the Superhero
Secure Access Service Edge (SASE), pronounced Sassy, is the latest buzzword amongst IT professionals. All the IT vendors are going on about it, but what is it, and what can it do for you?
I am here to break down the components of this latest IT trend and help you understand the technology behind the buzzword a little better.
An Origin Story
Gartner first coined the term SASE in 2019 and has been tracking vendor capability in this space for a while now.
Gartner publishes what is known as Magic Quadrants to rate where each vendor sits within a particular technology space. Whilst there is not a SASE-specific Magic Quadrant (yet), a good indicator is to follow both the SD-WAN and Security Service Edge Quadrants.
Is your network SASE enough?
Network engineering has come a long way in the past decade or so, other areas of IT evolved a lot quicker with the advent of cloud computing, but network engineering was a little slow to the party. Perhaps we network engineers love CLIs a little too much. However, we got there eventually. Virtualised networking gave us new ways to build and deploy appliances, leading to more adoption of public cloud, cloud-native architectures and Software as a Service (SaaS) platforms.
Security isn’t my problem, though? It’s all in the cloud, right?
Securing a network is becoming increasingly more difficult. Traditionally, the perimeter of the network used to be at the data center. Imagine a giant shield around your network, blocking any attacks from the outside world. Like our Gungan friends in Star Wars Episode One, All of their resources are contained behind the shield, safe from attack.

However, this is no longer the case, with a rise in SaaS platforms and remote working (especially after the pandemic) the perimeter is no longer centralised to your data center. Each of the homes accessing your corporate resources is now a perimeter, and each of the SaaS platforms housing your data is now a separate perimeter that you need to ensure is secure. And that list of locations is forever growing! You therefore need a shield for each of these locations. The Gungans used personal energy shields to solve their version of this problem, They really did think of everything!

But how do we solve our version of this problem now that the perimeter of your network is decentralised?
You used to be able to prevent access from the very edge of your network, this is no longer an option. How do you secure this new decentralised network? Can you be certain that the people accessing your data are who you expect?
Ask yourself this question, do you know who is using your network?
This is where SASE can be your shield.
But what on Earth is SASE… and how can it save us!
SASE is not a single product or technology, but it is a framework combining multiple security and network-related technologies. Each component can be deployed individually and can increase the security posture of an organisation, but together they become a security solution that deserves a cape.

Photo by Yulia Matvienko on Unsplash
SASE is the convergence of network and network security functions combined with the power of centralised cloud management. This whole concept would not be completed if it didn’t have more acronyms ( The IT industry loves acronyms don’t we, has anybody counted how many we use? ).
Gartner advises that solutions require five components to be a complete SASE solution and guess what, they are all acronyms.
What you need to be more SASE.

Zero Trust Network Access (ZTNA)
ZTNA is all about securing remote access to an organisation’s resources.
Traditionally, you would use a VPN to create a tunnel to connect your remote users to a data center hosting all the apps they needed. and this was great! We built encryption on top of the tunnels these solutions created and it was a secure way of putting your remote teams on the network. and that my friends, is the problem, the remote teams are logically on the network, you have just extended your network to a place you do not control.
Sure you may have a firewall in the path of traffic but this does not remove the fact that you are most likely provided network-level access to entire segments of the network that those teams do not need access to, and this can be exploited.
ZTNA changes the game a bit. ZTNA architectures work under the concept of ‘Never Trust, Always Verify’ which means that an endpoint needs to be explicitly allowed to an application or network resource. It is not implicitly assumed that because a user or device has remote access, they can reach the network resources.
This is pretty cool from a security perspective, If you are not meant to have access to an app, your traffic doesn’t even make it to the tunnel!
Not all ZTNA solutions are made equally some can do so much more than just be a gatekeeper for apps. (you may hear the term ZTNA 2.0 coined by Palo Alto Networks).
One of the cool features I’ve seen in a ZTNA solution is the ability to block network access if a device becomes non-compliant with the organisation’s policies.
Let me give you an example:
I am happily browsing away and I get blocked by that annoying AV product my company has put on the device. So annoying right? Well, luckily I am an admin on the PC, Ah Ha! I will just turn the AV off temporarily, No one needs to know.
With a traditional VPN, this would totally work and I can continue on with my access to the network, with ZTNA however, the endpoint client is monitoring the compliance of the device (does this device have AV turned on), and it sees my AV is now turned off so it blocks my access to the network.
I personally got excited when I first saw this, and just how quickly it dropped my access after turning the AV off.
Most security vendors have a ZTNA solution now, but be sure to really dig into the feature set, as I said earlier, not all are built the same.
Software-defined WAN (SD-WAN)
Oh! SD-WAN. If you are reading this, you will likely have heard of SD-WAN. If not, my post on SD-WAN will be ready soon!
A very brief primer, SD-WAN is the next-generation network architecture, which comes with a raft of benefits such as reduced cost, reduced management overhead, and higher utilisation of network resources.
Networks have different types of links to get you to your destination. Here are a couple:
- We have Private WAN links which were traditionally used to connect branch offices to Datacenters.
- We have Internet links which are provided by Internet service providers (ISPs) and connect your organisation to the Internet.
These links used to be expensive, and private WAN links generally still are.
With SD-WAN, cheap and cheerful Internet links can be bundled together to provide more bandwidth and connectivity options. To reach the datacenter, private WAN links can be maintained, or you can use the Internet links to reach your Datacenter. It does this using tunnels between offices, that are connected automatically.
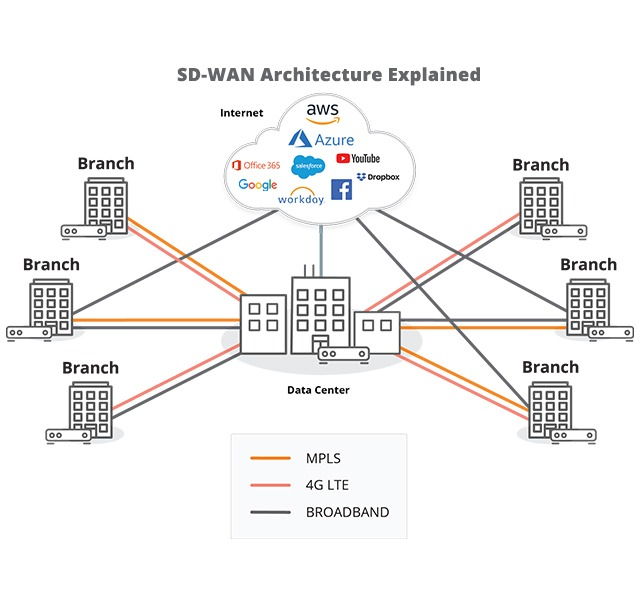
Image by HPE Aruba Networks – https://www.arubanetworks.com/faq/what-is-sd-wan/
One of the critical features of SD-WAN is policy-based routing. Imagine you’re driving on a road trip, and you come to a fork in the road. One path might be a bumpy old road, and the other might be a super smooth highway. You’d definitely want to take the smooth highway for a faster and smoother ride, right?
Well, SD-WAN looks at all the different paths the internet traffic can take to reach its destination, just like you have different roads to choose from. It figures out which path is the fastest, least crowded, and has the fewest bumps. Then, it tells your router to send traffic down that path.
It’s pretty cool when you think about it.
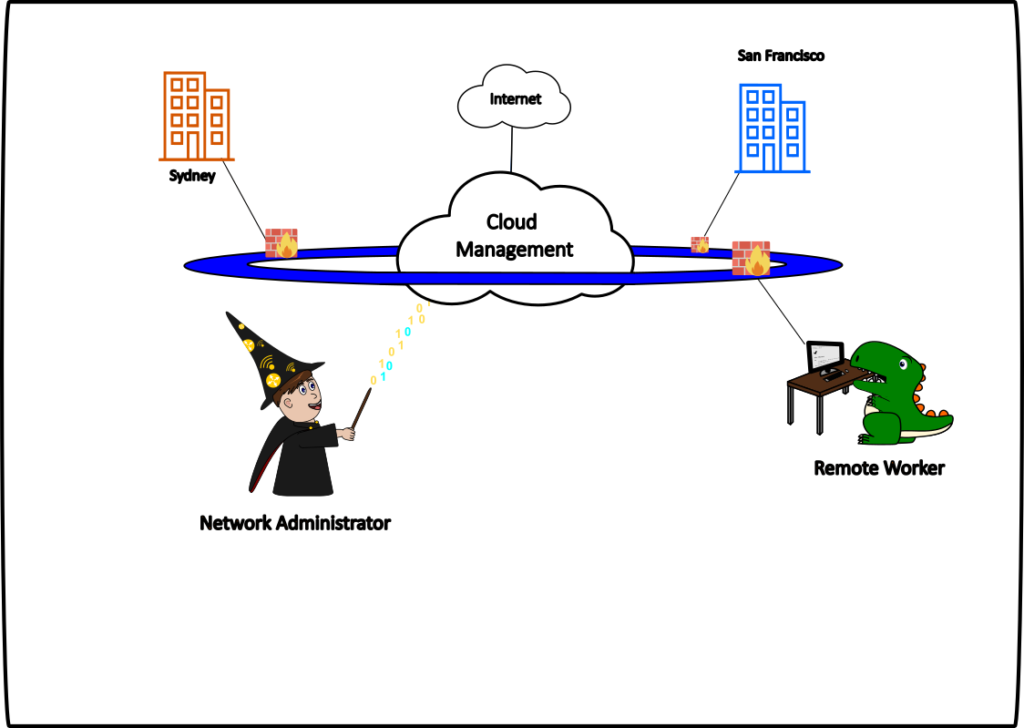
Firewall as a Service (FWaaS)
FWaaS is what it says on the tin. It is firewalling provided as a service by the SASE provider. Next-Gen firewall capabilities such as security policies and application inspection are provided by FWaaS, and utilise global Points of Presence (PoPs) to provide security close to the endpoints. This is all centrally managed in the cloud. This provides the ability to secure the edge of the environment across a globally diverse network and also provides a highly scalable architecture not burdened by the physical resources of hardware appliances or hypervisors in a data center.
It may be hard to imagine your perimeter firewall being duplicated across the world but this is essentially how it works.
Secure Web Gateway (SWG)
A SWG (Pronounced “Swig”) helps organisations keep their employees and systems safe while using the internet. The primary function of an SWG is to serve as an intermediary between end-users and the internet, facilitating secure and policy-compliant web interactions. Essentially it stops you from going to the bad places on the Web and stops them from coming into the network. One scene comes to mind to explain SWGs.

Cloud Access Security Brokers (CASB)
A CASB (Pronounced “Casby”) is a solution that helps organisations secure their data and activities as they interact with cloud applications and services. CASBs provide visibility into the use of cloud services within an organisation. They allow administrators to see which cloud applications are being used, who is using them, and what type of data is being accessed. They also enforce data protection policies to prevent sensitive or confidential data from being leaked or exposed. They can encrypt data, monitor data transfers, and prevent unauthorized sharing of information.
Unlike SWGs, CASBs are integrated with your cloud-based SaaS applications like Office365 and use this tight integration to enforce the data protection policies the organisation wishes to implement.
CASBs are useful in battling what is called shadow IT (where your users sign up to a SaaS App individually and use this app for work stuff, we have all done it!) CASBs can monitor what apps users are logging into and flag any unsanctioned apps. You can even configure policies to automatically prevent access to these apps, restrict their usage or even prevent the upload of files to them.
OK, great to know, but what does this mean? It all sounds like they do the same thing!
All the components I have talked about provide an improvement to the security of an organisation’s IT systems. Whilst some solutions do have overlapping capabilities, they are still a single piece of the puzzle. But just like a jigsaw, if you put all the pieces together, you see the whole picture!
As an organisation, if you invest in all of these components you will have complete visibility and control of what enters, and exits your corporate environment and what happens inside! You will be able to answer that one simple question, who is using your network?
Cyber attacks can come from any part of the technology ecosystem, including popular SaaS platforms. Technology has evolved and allows us to be more productive, and more efficient and who doesn’t love working from the beach!?
However, your security superpowers must evolve with it.
Many network and security vendors are introducing SASE products into their portfolios. It is always worth reviewing and validating solutions before diving in on one, the right partner can work with you to find the right fit for your environment and work with your infrastructure teams to build and implement this next-generation superhero.


One response to “SASE – Who is using your network?”
•
Great piece of information and simplified for users that don’t utilise the IT jargon on a day to day basis. Security is something that all institutions should be thinking about especially in this environment of evolving tech.